|
Sangeetha Sridhar Articles |
Other useful Articles

Cyber crime in the Social
media rising
Just like any other technology terror, victimization of members in social
networking websites is on the rise and lack of adequate security mechanism in
the deployment of these platforms compromises the security of its innocent
users. After understanding the dynamics of users and cyber criminals in this
context, we can also understand how the service providers are offering tools to
manage security scams.
Social media
Social networking websites promote active interactions between its users and
foster communities to interact using a range of multimedia tools. Content in
such sites is mainly user-generated and such content in the form of status
updates, images, audio and video help to increase interactivity among family,
friends, classmates, professionals, or groups of individuals with a common
interest. Due to a concentration of community members, even businesses and
governments have their corporate brand identity profile in such social
networking sites, engaging with their clients and potential customers is casual
dialog.
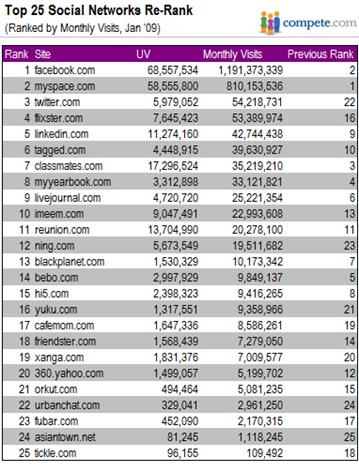
According to compete.com statistics, Facebook is the most visited social
network, with nearly 1.2 billion visits in January 2009, with MySpace at the 2nd
spot while Twitter on the 3rd place is growing rapidly at about
1,227% in just the 12 months.
Social challenge
The social networking sites are now attracting cyber criminals for reasons
including, intellectual arrogance, financial motives and other covert
intentions. While corporate post millions of damage due to security frauds and
malware, individuals are threatened by a loss of their privacy, data, and most
often their own identity. A mere hack into email account that has been active
for quite a long time can cripple the ownerís communications as the hacker
normally tends to change the password. Even if the password is only compromised,
it is possible to misuse the stolen identity and use it for impropriate or
fraudulent practices.
Complex technology systems have complicated security problems further. Security
is now a multi-fold approach requiring companies to build secure systems and
user to be aware and security scams and follow prudent guidelines. Social
networking sites who cannot afford to lose their userís trust are also taking
measures to avoid cyber crimes in their spheres.
A
recent attack on the micro-blogging service twitter.com, was launched through a
software worm compromising thousands of user accounts. Once compromised, the
userís confidential data and contacts can be sold in the dark market for its
worth. Users of Facebook, MySpace and other social networks have also been
targeted by phishing attacks forcing them to visit fake sites, whereby they are
tricked into sharing their identity or land up being infected with malware.
Twitterjacking scams, hacked into several celebrity accounts, including that of
Bill OíReilly, Barack Obama and Britney Spears. It is reputation damage when
fake tweets are posted in stolen identities as it happened in the case of CNN
anchor Rick Sanchez.
Facebook, Flickr and MySpace face several lawsuits for various privacy
violations including illegal use of private album pictures for marketing
purposes, exposure of email addresses, phishing scams, spam mails, etc.
Security Engineering
Security engineering is a sophisticated system of ensuring security in
real-world IT systems, by assuring confidentiality, integrity, availability,
authentication and non-repudiation. By these guiding principles, information
pertaining to users is maintained confidential in such a manner that only those
who are authorized can view / use it. There is good system to authenticate the
identity of a user and clearly mark his permission for doing certain selected
tasks. Despite all security measures in place the information, data or
application is continues to be available to legitimate users. Once a
communication or transaction is effected online, non-repudiation ensures that it
cannot be refuted.
Social Engineering
Security solutions that was
hitherto working well can now only resist technical attacks on systems and data,
however the weakest link in the security chain being the people themselves,
social engineering targets innocent victims to break security mechanisms in
place. Fraudulent messages, impersonating emails, fake phone calls are some
obvious modes that trick the naÔve users. Instead of painful technical attack,
cyber criminals find social engineering attacks on people more rewarding with
lesser efforts.
Potential threat
The user community posts
plenty of personal information on these social networking sites customizing them
for their network of friends. However as the Internet provides a sense of
anonymity, several fraudsters create innocent profiles to befriend and penetrate
into friendly networks. Inexperienced users, encouraged by the lack of physical
communications, tend to divulge sensitive private information in these public
platforms. Due to social pressure and encouraged by a false-sense of security,
the insight some user offer into their private matters is of serious concern.
There are fraudsters latching on to these fine details to launch more
sophisticated attacks on the innocent victims. Young children if not inducted
properly, can reveal plenty of private information about themselves and their
parents online.
Further information on who is
doing what and how to secure oneself while using these social networking
websites will continue next week.
The author is a technology evangelist working as consultant at
the Information Technology Authority of Oman and can be contacted at
sendsangita@gmail.com
or through her blog at
http://digitaloman.blogspot.com
or on twitter at
http://twitter.com/sangitasridhar.
Continued
Page 02
| 




